Defense and Hardware Assurance
Defense applications that require hardware assurance and long lifecycles are and ideal fit for FPGA and eFPGA solutions. FPGA or eFPGA based designs can be customized at development time and upgraded post deployment to add new features and functionality. This is particularly important because security measures degrade over long periods of time when they are susceptible to outside threats. Reprogramming an FPGAs or eFPGAs allow a design to be adapted to changing threat profiles and to new attack methods by adding or modifying an IP block specifically designed to combat those vulnerabilities. Critical IP blocks can be added very late or remotely in the field which ensures that the majority of the manufacturing and supply chain will never come into contact with these critical IP blocks, even in their encrypted form.
The Speedster7t FPGA family is optimized for high-bandwidth workloads and eliminates the performance bottlenecks associated with traditional FPGAs. Built on the TSMC 7nm FinFET process, Speedster7t FPGAs feature a revolutionary new 2D network-on-chip (2D NoC), an array of new machine learning processors (MLPs) optimized for high-bandwidth and artificial intelligence/machine learning (AI/ML) workloads, high-bandwidth GDDR6 interfaces, 400G Ethernet and PCI Express Gen5 ports. The 2D NoC connects all of the interfaces to over 80 access points in the FPGA fabric to deliver ASIC-level performance while retaining the full programmability of FPGAs. Get started today with the VectorPath accelerator card, featuring the Speedster7t FPGA.
Hardware Assurance Risks
Using an FPGA or eFPGA based solutions helps to overcome many of the inherent risks that are found when implementing solutions in a custom ASIC device. These hardware assurance risks are:
- Fraudulent Products – Counterfeit and non-genuine devices, possibly even obtained from legally authorized sources, which could include production overruns, relabeled, recycled, cloned, defective, and out-of-spec devices.
- Malicious Insertion – The intentional insertion of malicious code or defects to degrade performance or cause mission failure. Malicious insertions could include logic bombs, Trojan "kill switches" and back doors for unauthorized access to control logic functions and/or alter data.
- Tampering – Unauthorized extraction of sensitive intellectual property using reverse engineering, side-channel scanning, run-time security analysis, and embedded-system security weaknesses.
- Quality Escape – The introduction of product defects, deficiencies, vulnerabilities, or product inadequacies either by mistake or through negligence during the design, production, or post-production handling of a device or system that degrades the product's performance at any time over its entire life cycle.
- Emerging threats – New threats, such as counterfeit component trends, security attacks, and trust issues that combine two or more existing threats into a new vulnerability exploit.
Achronix FPGA and eFPGA Solutions
Achronix is the only company that offers high-performance, standalone FPGA and eFPGA IP solutions for defense applications. The Speedster7t FPGA and Speedcore eFPGA IP incorporate advanced encryption and authentication security features such as:
- RSA public/private key authentication before the block starts to decrypt a configuration
- 256-bit AES-GCM encryption to provide strong encryption and authentication of the configuration
- Rotating keys and DPA countermeasures used to protect against side-channel attacks
- Secure key stores leveraging physically unclonable functions against cloning and overbuilding
ASIC with eFPGA Supply Chain Security
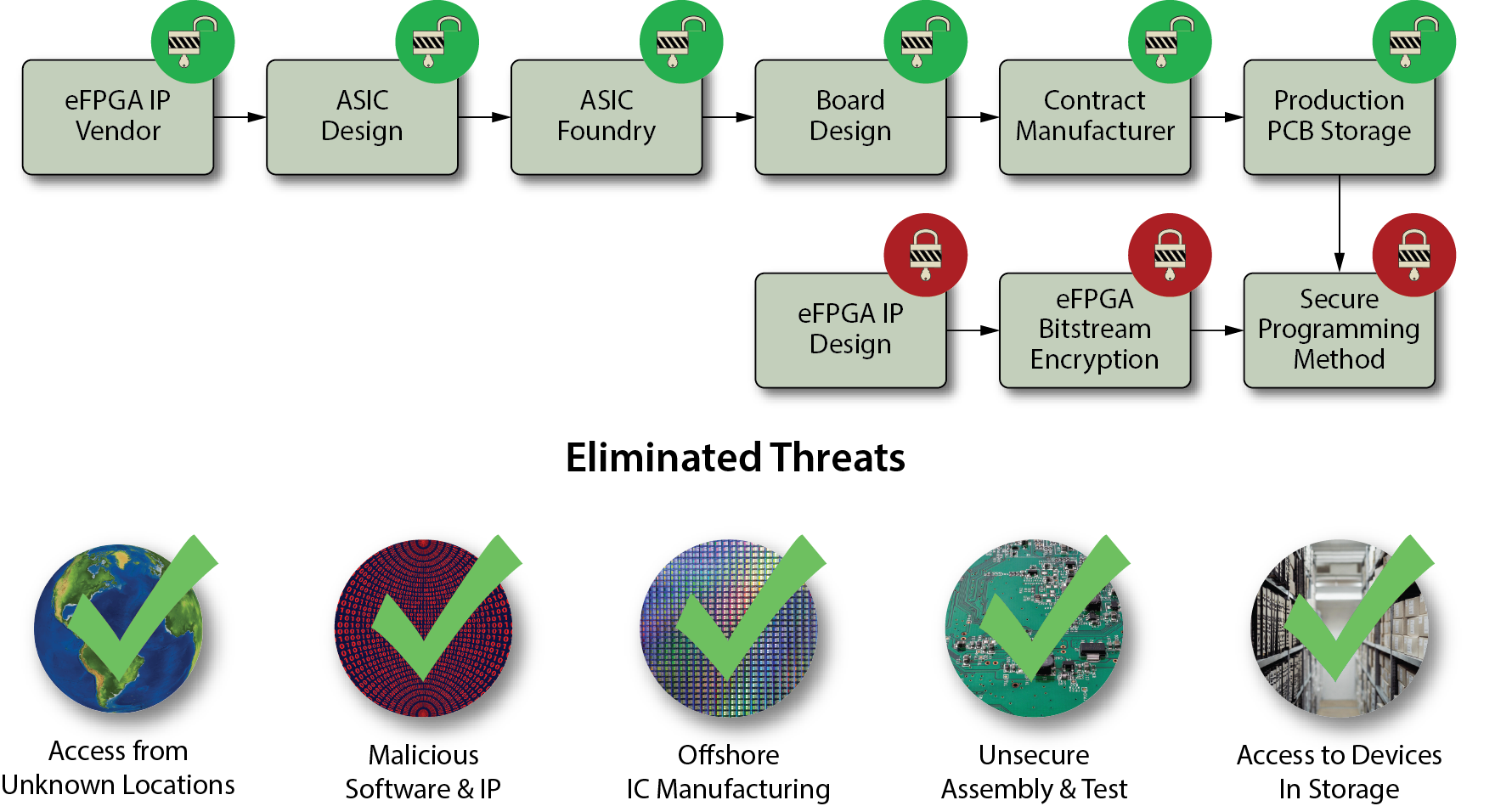
Achronix eFPGAs benefit from the inherent security advantages of our standalone FPGA technology and can also extend product lifecycles through in-field and remote updates. Compared to an ASIC only design, an ASIC with eFPGA allows defense manufacturers to add hardware assurance capabilities that simplify the security of the ASIC supply chain. As shown in the supply chain diagram below, there are fewer opportunities to tamper with the design vs an ASIC only approach. The threats can be controlled by securing the development, encryption and programming of the eFPGA IP. Defense manufacturers can also keep their ASIC supply chain security separate and mitigate risks associated with the ASIC manufacturing process such as access to the ASICdevice from unknown locations, insertion of malicious software and IP, ability to compromise the assembly and test of the ASIC and access the ASIC in long-term storage facilities. Since the critical IP is stored in the eFPGA, these devices will not contain any sensitive design information until they are remotely programmed in the field or a secure location.
Supply Chain Security for eFPGA Design